Security Monitoring
Security Monitoring
Protect your company data
Think of your business with your data as a building that needs to be protected from attacks that come from outside but also from within. By implementing an effective monitoring strategy, you can detect and mitigate threats faster before they can spread. With security monitoring from NFIR, you can proactively detect and respond to threats before they do damage.
Another important benefit of security monitoring is that it can help detect potential vulnerabilities in your network and systems. This can help you quickly identify and fix these vulnerabilities before they are exploited by cybercriminals.
Security monitoring
The process of security monitoring involves continuously collecting and analyzing data about your network and systems. This includes monitoring events and activities, identifying anomalies and performing analysis to detect potential threats. When threats are detected, immediate action can be taken to stop the threat and mitigate the damage. We view your business with your data as a building that need to be protected from attacks that come from outside in, but also from inside out. Our security monitoring does this proactively by creating use cases that “go off” when a threat occurs. We categorize this threat within the team. Then we agree with you accordingly on what we do.
This is why security monitoring by NFIR
At NFIR, we understand how important it is to protect your business from cyber threats. That’s why we offer a comprehensive security monitoring service that protects your business from the latest threats 24/7. Our security monitoring service offers several benefits to your business:
-
Real-time detectie en respons op bedreigingen
-
Proactieve monitoring en dreigingsinformatie
-
Diepgaande analyses en rapportage
Dit helpt u bij het identificeren van kwetsbaarheden en het nemen van proactieve maatregelen om uw bedrijf te beschermen
-
Maatwerkoplossingen
-
Verbeterde productiviteit
Onze monitoringoplossing helpt uw bedrijf om de productiviteit te verhogen door onnodige downtime en storingen te minimaliseren die worden veroorzaakt door cyberaanvallen
-
Kostenbesparing
-
Naleving van wet- en regelgeving
-
Verbeterde reputatie
Onze monitoringoplossing helpt uw bedrijf de reputatie te beschermen door te voorkomen dat vertrouwelijke informatie in handen komt van kwaad willenden en door de downtime als gevolg van aanvallen te minimaliseren
NFIR is a Dutch company that communicates with you in Dutch, verbal conversations as well as reports and analyses are in Dutch. Also, all data is stored in the Netherlands.
The connection process of security monitoring
NFIR offers an A-Z complete service. This means that we work with you from multiple disciplines from the intake. During the implementation phase, a team is assembled consisting of a business consultant, a security engineer and a project manager. This team will be in constant communication with you. Together with this team, you determine what the “use cases” – aka security rules – are on which the alerts go off. The final solution offered by NFIR is a 100% automated solution to monitor your network operations.
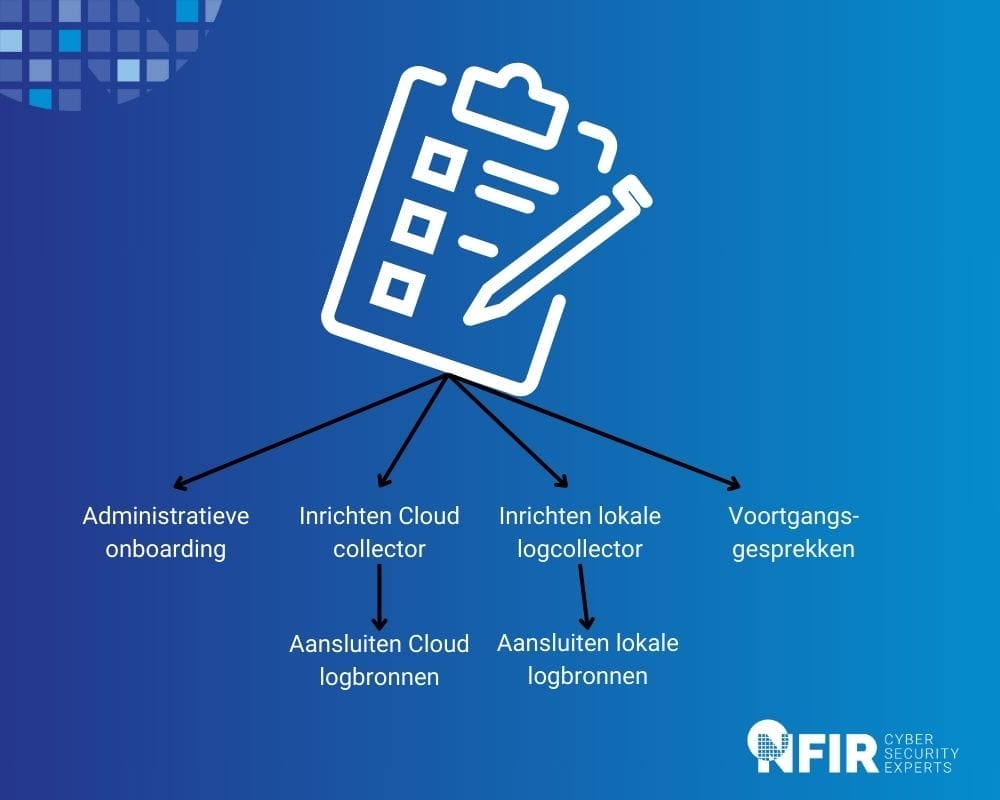
This is how security monitoring works
You will receive critical notifications immediately via email or text message and can take action on them yourself. We filter the notifications and alert you only if we deem it necessary.
As the service gradually runs within your organization, a service manager will also be added to the team. After completion, he or she will go through all the reports with you every month. Based on this, the service manager will indicate how this process can be optimized.
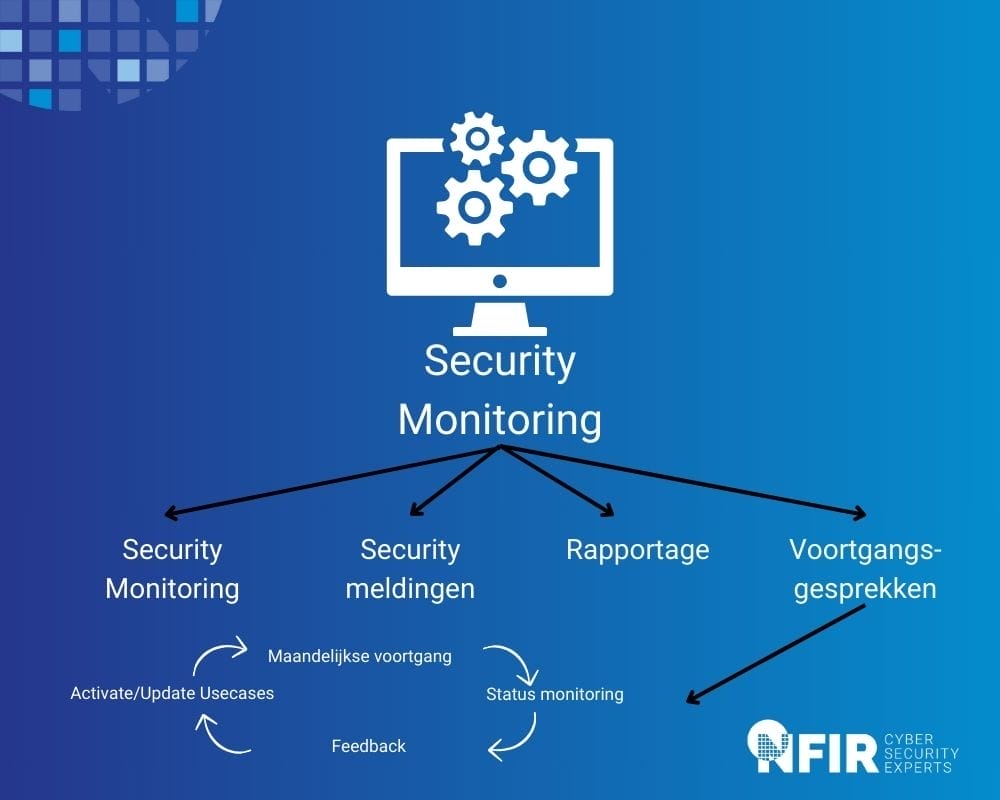
You can already do this yourself
It is important to continually update and adapt cybersecurity risk protection to the changing threat landscape. You can probably do this yourself to reduce the risks.
- Keep software and systems up-to-date with security patches.
- Use strong, unique passwords and multifactor authentication (MFA) whenever possible.
- Train employees in security awareness, including how to deal with phishing attacks and social engineering.
- Implement robust security policies and conduct regular security reviews.
- Use advanced security solutions such as next generation firewalls, antivirus software, and intrusion detection/prevention systems (IDS/IPS).
- Limit access to sensitive information and manage user rights carefully.
- Plan and practice an incident response plan in case a security incident occurs.
- Review supplier and partner security measures to reduce the risk of supply chain attacks.
- Monitor and manage employee access rights to mitigate insider threats.
- Limit the use of administrator privileges and application whitelisting.
- Keep systems up-to-date and install security software.
Security monitoring for everyone
At NFIR, we believe that security monitoring should be accessible and available to all businesses. Because we offer this service at a very affordable price and because it can be easily interpreted at any company, this service is also suitable for SMEs (companies with 50 to 500 employees). Of course, security monitoring is also suitable for the very largest companies in the Netherlands.
Frequently asked questions
What is Security Monitoring?
Security monitoring involves monitoring network traffic and analysing log files in order to detect threats, vulnerabilities and cyber attacks at an early stage. Because interpreting logs and investigating reports cannot be done effectively without underlying knowledge of the (customer) network, we focus on the collaboration between security monitoring and management. We help you discover vulnerabilities in your policies, configurations or network. We do this through regular progress meetings, helpful reporting and knowledge sessions. The knowledge sessions are based on the MITRE Defend framework and contribute to the maturity of your organization.
How is network traffic monitored?
Log sources are connected to the network. Log sources are important servers or applications that generate log files. These log breaking states are sent to a SIEM. This is a central server where all log files are collected. In this SIEM, automatic detection rules search the log files. When a suspicious pattern is detected, this detection rule will generate a notification. This notification is investigated by our security engineers in the Security Operations Center (SOC). If the report is alarming we will contact you.
How can security monitoring help secure my network?
Monitoring your network can help detect malicious behaviour early on. If you want to protect your network, it is best to start monitoring your network. You gain insight into your network, you are quickly informed of suspicious activities and you can take appropriate action if a suspicious situation arises.
On what basis does NFIR develop its monitoring service?
We develop our monitoring service by closely monitoring cyber security developments and adapting our detection rules accordingly. Furthermore, we continuously optimize our detection rules. We also constantly seek coordination with you as a client about current events that affect you and discuss security topics with you through short knowledge sessions.
Managed Detection and Response (MDR).
Our Managed Detection and Response (MDR) service is designed to protect your data and interests even when a threat evades organisations’ general security controls. Our MDR security platform is an advanced 24/7 security control that covers a range of fundamental security activities, including cloud managed security for organisations that cannot maintain their own security centre. In addition to securing your company’s data and customer data, the government, with the GDPR (AVG) legislation, also requires you to take appropriate measures to protect personal information where you are a data controller or processor.

