Personal Health Environments (PGOs)
A personal health environment (PGO) is a website or app, in which you can keep track of information about your own health and actively get to work on your health. This allows you to collect and manage your medical information, but also to share it with others. This way you keep a grip on your health data. From treatments to lab results, medications and vaccinations. And this data will remain available your whole life.
Information security of the PBL
In striving for a sustainable information system for healthcare, the national Healthcare Information Council has drawn up a number of programmes. One of those programs is MedMij, in which the security of the personal health environment (PGO) is laid down.
See: https://afsprakenstelsel.medmij.nl
MedMij’s goal is to ensure that everyone who wishes to do so has access to his or her medical data in a safe manner. MedMij offers both technical and legal standards and guidelines for the accessibility of data and the exchange of data. One of these standards is HL7 FHIR, which has been developed as an easy-to-use format for the exchange of healthcare information.
In order to qualify for a MedMij declaration as a healthcare organization, you must be able to demonstrate that the PGO is safe and reliable. One of the ways to demonstrate this is a NEN7510 certification and the annual testing of the technical resilience of the PGO’s software by means of a penetration test.
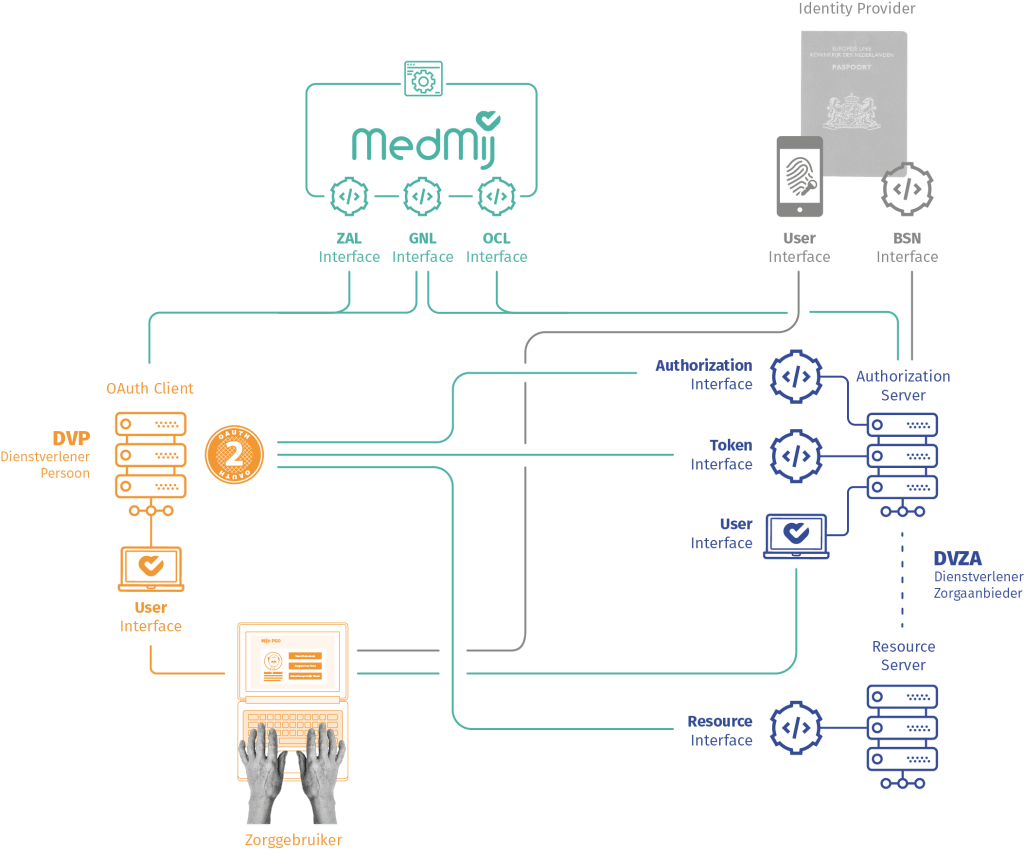
Penetration test requirements of MedMij
At least annually, a Grey Box application penetration test should be performed on the external interfaces by an external, independent organization. Before joining MedMij it is important that this pen test has already taken place at least once and the high and medium risk findings on external MedMij interfaces have been resolved.
The following specific MedMij requirements must also be demonstrably tested in the pentest report;
- DNSSEC see core.dns.300 and core.dns.301
- TLS see responsibility core.tls.301 in conjunction with core.tls.302 and core.tls.304
- NCSC web application guidelines U/PW.02, U/PW.03, U/WA.03, U/WA.04 Note these are already required for DigiD assessments. See NOREA Handreiking DigiD assessments.
For accession, it has already taken place at least once and MUST have resolved the high and medium risk findings on external MedMij interfaces.
For penetration tests performed after accession, an adequate action plan should be prepared for at least the high and medium risks (CVSS (Common Vulnerability Scoring System) score of 4.0 or higher) with respect to the MedMij service. This action plan is shared with the management organisation. Corrective actions are implemented in a timely manner.
A Grey Box penetration test involves the penetration tester having as much insight into the application as possible. This may include, among other things:
- Access to architecture/design documentation;
- Access to source code;
- Login data for different roles.
It is not necessary to perform a penetration test on the entire architecture and/or all program code. In particular, it is about the security of the data exchanged over the Internet, so the focus should be on the security of the external interfaces. An app or web portal is also an external interface!
For more information about the pen test requirements, please click here.
Grey Box pen test by ethical hackers from NFIR
To ensure that the (web) applications, interfaces (APIs) and underlying infrastructure developed by your organization are free of vulnerabilities and meet the requirements set within the MedMij agreement framework, you are expected to have a Grey Box pen test performed. The ethical hackers are provided with the source code in order to have maximum insight into the functioning of the developed software.
After the NFIR has carried out the pen test, you will know exactly where you stand. The vulnerabilities found are presented to you in a clear and complete report. This includes a management summary and an advice per vulnerability with the solution direction. Each vulnerability is fully reproducible, so that you can work in a targeted manner to eliminate these vulnerabilities. A re-test offers the ultimate certainty that the previously found vulnerabilities have been adequately remedied.
We not only test (web) applications, interfaces (APIs) and the underlying infrastructure for you. If you provide mobile applications, these can also be subjected to a pen test by our ethical hackers. All roles and rights are reviewed on the basis of internationally recognised methodologies. In addition, the creativity of the hackers is used not only to test the “happy flow” but also to assess less common flows. Precisely these less common flows are often forgotten, but are very important to test for possible vulnerabilities. After all, the data processed by the PGOs are often special personal data, so it is especially important to test them thoroughly.
Please contact us for more information and a no-obligation intake.
Penetration test?
NFIR classifies pen testing vulnerabilities using the Common Vulnerability Scoring System (CVSS 3.1).
Why hire the ethical hackers from NFIR for pen testing?
NFIR is a specialist in the field of cyber security. We help organizations limit the consequential damage of a cyber incident and secure digital forensic evidence to identify the cause of the damage. In addition, our services can help you increase your resilience against cyber incidents and support you in improving your digital vital infrastructure. Our experienced staff, all of whom have received approval from the chief of police, are able to support and advise you in a no-nonsense way with our preventive services (awarenesstrainings, pentesting and security monitoring) and reactive services (incident response and digital forensics).



