The goal of our MDR services is to unburden and support your organization in the area of Security Monitoring. NFIR monitors the most common log files of the agreed network components 24/7/365 and provides adequate analysis, follow-up actions and reports according to the agreements made. Through logging, monitoring and detection measures, NFIR ensures that cyber threats and attacks can be detected at a very early stage. Through early detection, adequate action can be taken to stop the attack as quickly as possible or, in some cases, even prevent it. Also, central logging -separated from the network- ensures that in the event of an incident, forensic investigation is guaranteed. After all, malcontents could cover their tracks.
The importance of adequate logging
When conducting forensic investigations, maintaining logging with integrity comes back as a concern to our clients. Logging is not only a requirement for compliance goals, but also provides insight into what has occurred from a risk perspective. NFIR hereby takes care, at a minimum, of tuning the detection for the presence of logging and reading in logging in an established format for analysis. Then, easy and fast retrieval of information is a next step that we support clients with. With logging stored outside the system landscape, irrefutable proof of certain behaviors at the system level has become much easier. As a side effect, the preventive effect on malicious behavior of users or hackers is also made transparent, so that it can be mitigated in terms of risk following an integer process. Connection of such logsources requires an integrity check and can then be arranged with simple use cases. This integrity check should ensure that the logging can be trusted by providing visibility and hardening of system usage. Another reason for storing logging is to provide insight about attacks and/or anomalous behavior and other vulnerabilities.
The use of logging is necessary for storing important information from the network. There are two reasons for this:
- Logged data can be analyzed and activated through use cases.
- Log data is very important to serve as a forensic basis for digital forensics in case of incidents.
Use case development
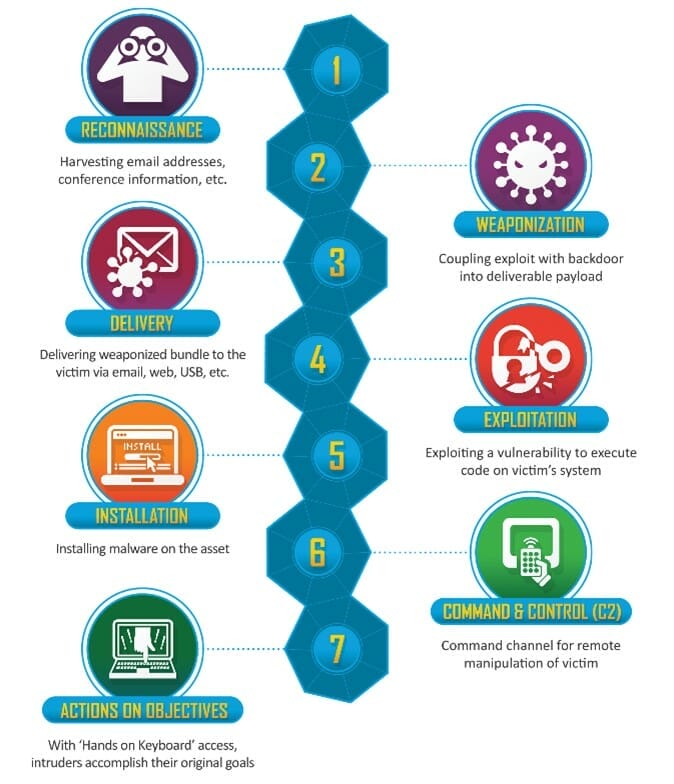
As a starting point for use case development, we assume the risk of information being compromised by criminals who use it for monetary gain or extortion. This is a risk scenario where modifications by the attacker succeed each other. Consider the growing phenomenon of “ransomware” as well as the ex-filtration of classified information. Criminals bypass detection measures that indicate the building of such an attack. This requires an understanding of how to detect these build-up activities, these activities are also referred to in the cyber security market as the “Cyber Security Kill Chain. See below for a representation of the common steps involved in this chain that can be taken and result in a successful attack.
The steps in this “Cyber Security Kill Chain” have been developed as an attack scenario. However, it is also possible that other paths could be used leading to a variety of scenarios. Therefore, the translation into use cases remains a constant development that NFIR focuses on based on the constant supply of knowledge from various experiences.
To illustrate, we outline below the possible use cases per attack step, these use cases are usually smooth to implement and provide a good basis.
|
Attack step |
Use case |
|
Discovering vulnerabilities in the environments |
Open RDP ports that are accessed from the outside |
|
Attempts at account abuse and/or modifying permissions |
Detection of brute-force attacks within the local Windows domain Detection of brute-force attacks within Azure AD |
|
Attempts at account abuse and/or modifying permissions: Communication appropriate to attacks |
Creation of mailbox rules via Exchange Online web portal |
|
Attempts at account abuse and/or modifying permissions: Command & Control |
Abnormal login attempts with accounts within Azure AD |
|
Adjusting settings. For example DLP policy, phishing filter. Etc. Catch all, for analysis |
Monitoring Threat Intelligence findings. |
|
Communication appropriate to attacks: Catch all, for analysis |
NFIR analyzes and combines threat info from firewall with other log sources to provide a holistic view. |
In a nutshell
The first step is to link your log sources via a so-called log collector with the 24/7 functioning SOC, for Network Monitoring. Information from log sources from, for example, an intrusion detection system (IDS), firewall, Active Directory, endpoint detection, Microsoft365, Windows event logs are linked to our SIEM. You then work with our team to determine what the use cases are that specific alerts should go off on. Critical notifications will be sent to you from our SIEM/SOC immediately via email or text message and/or you will be called. Your ICT department can take action on this. Our service is managed: we only alarm when necessary. Once the service has been running within your organization for a while, you will have a service manager as standard who will go through all the reports with you each month and advise on how the MDR process can be further optimized.
Interested in our Managed Detection and Response (MDR) solution?
What is Security Monitoring?
Security monitoring involves monitoring network traffic and analysing log files in order to detect threats, vulnerabilities and cyber attacks at an early stage. NFIR offers a fully automated solution, so that you no longer need to interpret data yourself. Via a dashboard you can view all notifications and take action if necessary.
How is network traffic monitored?
NFIR Insights, our security monitoring service, analyses all data from the connected detection sources and displays that processed data in an easy to interpret dashboard environment. NFIR’s security monitoring specialists automatically process the log data received on the basis of use cases, which are determined together with the customer. When monitoring network traffic, all information, including reports of suspicious activity, ends up in a dashboard. This way you are quickly informed of activities on your network and you can intervene adequately in case of suspicious activities.
How can monitoring security help protect my network?
Monitoring your network can help detect malicious behaviour early on. If you want to protect your network, it is best to start monitoring your network. You gain insight into your network, you are quickly informed of suspicious activities and you can take appropriate action if a suspicious situation arises.
How is network traffic monitored?
NFIR Insights, our security monitoring service, analyses all data from the connected detection sources and displays that processed data in an easy to interpret dashboard environment. NFIR’s security monitoring specialists automatically process the log data received on the basis of use cases, which are determined together with the customer. When monitoring network traffic, all information, including reports of suspicious activity, ends up in a dashboard. This way you are quickly informed of activities on your network and you can intervene adequately in case of suspicious activities.
What is the significance of SIEM and SOC?
NFIR offers a scalable, manageable and affordable solution with its Security Information and Event Management (SIEM) and the implementation of a Security Operation Centre (SOC). We offer our SIEM as a fully automated solution, where you no longer have to interpret data yourself. The outputs are reports that your IT department can take action on. Read how we take the worry out of your life and what results you will achieve when implementing our SIEM and SOC solution.