The number of ransomware attacks in the Netherlands is large and even increasing. In a recent survey, nearly three-quarters of Dutch companies surveyed said they would be hit by a ransomware attack by 2021. Only slightly more than a third said they had a cybersecurity strategy ready. This is while the impact of a ransomware attack on your business or organization is enormous. Your business operations are severely hampered or even made impossible. Trade secrets (can) be resold and data leaked. Your external partners no longer trust your organization and take a wait-and-see attitude. And don’t think “that won’t happen to us,” because it can happen to anyone. From large companies and organizations to SMEs employing 20 people.
What is ransomware?
Ransomware is malware that encrypts a user’s data files and later decrypts them to demand a ransom. In extreme cases, ransomware blocks access to IT systems by also encrypting system files that are essential to the proper functioning of the system. Given the destructive nature of ransomware attacks, it is often difficult to recover log files to understand what really happened. Decrypting ransomware requires specialized knowledge and skill. Hackers may have stolen intellectual property and personal information and used ransomware to hide their true intentions.
Examples of ransomware
In general, two types of ransomware can be distinguished: locker ransomware and crypto-ransomware.
Locker ransomware: this form of ransomware locks access to the screen of the infected device. Users can no longer use basic computer functions. One way this manifests itself is not being able to use keyboards and a mouse.
Crypto-ransomware: this form of ransomware encrypts files on the infected system. This is done through encryption algorithms. Its main purpose is to encrypt critical files. In this form of ransomware, the computer’s standard functions remain unaffected. Not having a complete and quality backup can make the consequences of a crypto-ransomware attack unprecedented for an organization. A well-known example of crypto-ransomware is the WannaCry software. This ransomware was developed specifically for the Microsoft Windows operating system. In 2017, an outbreak occurred in which more than 230,000 Windows computers were infected. What both locker and crytpo ransomware have in common is that both forms require a ransom in exchange for decryption.
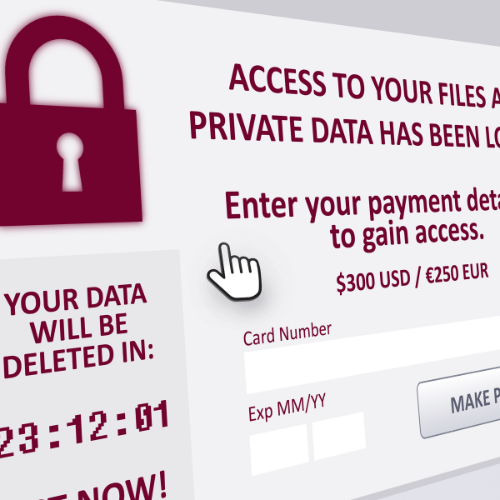
How does ransomware get in?
Your organization’s systems can become infected with ransomware in a variety of ways. Often the ransomware is spread by a (targeted) email, also known as spear-phishing. Cybercriminals pretend to be a colleague or someone from a friendly organization. The attachment of the email contains the virus. When someone opens the attachment, an attacker gains access to systems. From there, an attacker proceeds to map the organization. Soon, your organization will receive notification that systems and/or files are no longer accessible. These are in fact encrypted. The hostage taker promises to decrypt the whole thing again after paying a ransom. However, if you do not pay, the same attacker promises to make all your stolen data public. However, there are also cases of entering via an open RDP (Remote Desktop Port, to log into the work computer at another location such as home) or exploiting known but unresolved vulnerabilities in systems. Then just visiting an infected website is enough to get infected.
What happens after attackers gain access?
After gaining access to your system, the attacker looks around at his leisure and forms a judgment. Where is he actually within your systems? But also: what type of organization is your company or institution and how much ransom could you pay? For example, one looks for the financial statements to make a good estimate. Next comes the phase of stealing information in large volumes. This can be all kinds of data. From private data of your employees and customers to invoices/bills, complaints, legal documents and internal documents about your business operations. This concerns generally sensitive information. This phase can last up to several months. The final step is to carry out the ransomware attack itself, by holding your computer systems and files hostage.
A ransomware attack has a major impact on your organization
When your organization is affected by a ransomware attack, it usually becomes known to your customers, partners and associates fairly quickly. It is in itself a fundamental hindrance to your day-to-day operations, which, for some time at least, come to a total halt or, at the very least, are severely disrupted. Business data, trade secrets and/or data of your customers, employees and or partners can also be leaked. On top of that, all of your relationships, from partners to customers, will take a wait-and-see approach until you have convinced them that the situation has returned to normal and your systems can be trusted again. If you have agreed to service level agreements (SLAs) with your customers, then a legal aspect also comes into play.
What can you do yourself to prevent a ransomware attack or limit the impact?
- Incident Response Readiness: ensure that your company has an Incident Response plan, possibly supplemented by an Incident Response Retainer (IRR) so that your are assured that when the situation does occur, you will be provided with adequate and professional services to mitigate the impact and damage and return operations to normal as soon as possible.
- Managed Detection and Response (MDR): make sure you have a functioning system in place to monitor activity on your network and actively detect an attack. This way, you can take quick action to limit the impact of the attack.
- Provide a compartmentalized computer network, with sections automatically locked as soon as an attack is detected. Compare it to a physical building where fire doors and fire-resistant partitions successfully slow down the fire.
- Use the 3-2-1 backup principle. Provide 3 copies of key dates. Keep those backups on at least 2 different media (for example, a hard drive and tapes). Store 1 copy outside the door. In fact, you cannot assume that the ransomware is guaranteed to decrypt.
How can NFIR help if you face a ransomware attack?
Your own IT department undoubtedly has very well trained and competent staff. However, it is wise to seek expert assistance. Our Computer Emergency Response Team (CERT) will come to you quickly if required. The experts on this team have years of experience with cybersecurity in all its facets, making them true ransomware specialists. After an intake, we first focus on possible mitigation measures to minimize the impact of the ransomware attack. At the same time, we start our in-depth research for a complete analysis of your situation. From this, a number of specific recommendations flow. We can also assist with your communication of the resulting situation.
ransomware, malware, files, ransom, ransomware attacks, user, software, payment, para, cryptolocker, malwarebytes, trojan, windows, malicious, encrypted, encrypting, risk, microsoft, hipaa, hackers, backup, extortion, security, wannacry, anti-malware, cryptoviral extortion, petya, intrusion prevention, malware attack, cryptowall, doxware, gameover, bad rabbit, ryuk ransomware, cryptolocker, malvertising, phishing, social engineering, virus scanner, locky, ids, private key, ips, hipaa, updates, asymmetric encryption, antivirus, police trojan, protected health information, global cyberattack, attack, malware, data, cyber, computer, cryptolocker, bitcoin, encrypted, kaspersky, infected, protection, message, petya microsoft, police, healthcare, awareness, hacker, android, logo, locky, anonymous, infographic, nhs, lock screen, wallpaper, wanna cry, screenshot, poster, transparent, ransomware, malware,
ransomware, attacks, security, attack, data, malware, files, ransom, computer, software, access, victim, device, business, system, protection, que, payment, user, devices, encryption, network, threat, systems, key, users, attacker, para, attackers, organizations, malwarebytes, organization, types, victims, threats, response, data, windows, risk, money, ransomware attacks, ransomware attack, private key, united states, malicious software, decryption key, mobile ransomware, mobile devices, crypto ransomware, ransomware protection, business associates, ransomware attackers, screen lockers, different types, asymmetric encryption, ransomware infection, bad rabbit, min read, government agencies, ransom payment, data hostage, low probability, ransomware ransomware, sensitive data, security software, hard drive, social engineering, colonial pipeline, ransomware strains, recent years
files, ransom, ransomware attacks, user, software, payment, para, cryptolocker, malwarebytes, trojan, windows, malicious, encrypted, encrypt, risk, microsoft, hipaa, hackers, backup, extortion, security, wannacry, anti-malware, cryptoviral extortion, petya, intrusion prevention, malware attack, cryptowall, doxware, gameover, bad bunny, ryuk ransomware, cryptolocker, malvertising, phishing, social engineering, virus scanner, locky, ids, private key, ips, hipaa, updates, asymmetric encryption, antivirus, police trojan, protected health information, global cyber attack, attack, malware, data, cyber, computer, cryptolocker, bitcoin, encrypted, kaspersky, infected, protection, message, petya microsoft, police, healthcare, awareness, hacker, android, logo, locky, anonymous, infographic, nhs, lock screen, wallpaper, wanna cry, screenshot, poster, transparent
ransomware attack, ransomware removal, ransomware attack, ransomware examples, ransomware linux, prevent ransomware, ransomware translation, ransomware software, ransomware attack, ransomware examples, ransomware prevention, ransomware wikipedia, ransomware netherlands, ransomware news, ransomware attack, ransomware meaning, ransomware attack 2021, ransomware definition, ransomware decryptor, ransomware removal, ransomware as a service, ransomware virus, ransomware conti, ransomware wannacry, kaseya ransomware attack, kronos ransomware attack, kronos workforce ransomware attack, kronos ransomware, conti ransomware, darkside ransomware kaseya vsa ransomware attack, revil ransomware, accenture ransomware attack, accenture ransomware,
virus, ransom, malware, human operated ransomware, back up, cyber, ransomware attack, ransomware attacks, cybercrime, hackers, cybersecurity, attacks, security, ransomware attack, ransomware attacks, antivirus, hacked, hack, cyber attack, security, big ransomware, hackers, cybersecurity, revil ransomware, computer, computable, cyber security, ransomware attack, a ransomware
What is ransomware, How does ransomware work, How can I protect myself from ransomware, What should I do if I'm a victim of ransomware, How can I remove ransomware, What are the different types of ransomware, How can I prevent ransomware, Is there a way to decrypt ransomware, What is the best way to protect against ransomware, How do I know if I have ransomware, What are the symptoms of ransomware, What causes ransomware, How does ransomware spread, What is the history of ransomware, Who creates ransomware, Why do people create ransomware, How much does ransomware cost, How much do ransomware victims pay, Can I get my money back if I'm a victim of ransomware,
Security incident? Get acquainted with incident response
Our incident response team is available 24/7 to identify and resolve any cyber incident
What is ransomware?
Ransomware is malware that encrypts a user’s data files and later decrypts them to demand a ransom. In extreme cases, ransomware blocks access to IT systems by also encrypting system files that are essential to the proper functioning of the system. Given the destructive nature of ransomware attacks, it is often difficult to recover log files to understand what really happened. Decrypting ransomware requires specialized knowledge and skill. Hackers may have stolen intellectual property and personal information and used ransomware to hide their true intentions.
What is the difference between ransomware and malware?
Ransomware is a type of malware that encrypts a victim’s files and demands a ransom to decrypt them. Malware, on the other hand, is an umbrella term for all types of malicious software, including viruses, Trojans, worms and spyware. Although ransomware can be considered a form of malware, not all malware is ransomware.
How do you prevent your organization from becoming infected with ransomware?
Ransomware is on the rise, no one will deny that anymore. Where once the goal was to gain access to bank accounts, attackers are now getting paid to decrypt victims’ files.
Read the full article: How do you prevent your organization from becoming infected with ransomware?
When am I dealing with a reportable incident data breach?
At the moment that unauthorized persons (can) access personal data, there is a potential data breach. In many cases, organizations are required to report the incident to the Personal Data Authority (AP). The AP was established and designated as the regulator of the General Data Protection Regulation (AVG) and the AVG Implementation Act (UAVG). When a data breach occurs depends on the circumstances. For example, a data breach need not be reported if the risk to rights and freedoms of data subjects is limited. This is in contrast to when an unauthorized person gains access to a customer’s passport or bank account number. After all, in that case, misuse of identity or financial consequences cannot be ruled out. Such incidents must be reported to the AP within 72 hours.
Read more: When am I dealing with a reportable incident/data breach?
Can I always contact NFIR to get help in case of an IT-Security incident?
Yes, we are available 24/7 for SMEs, multinationals, government bodies, educational institutions and non-profit organisations. Within three hours, an incident response (CERT) team is present at every location in the Netherlands (Wadden Islands excluded).
NFIR is an official CERT but what does that actually mean?
CERT stands for Computer Emergency Response Team. The attribute is awarded by Carnagie Mellon University to companies and teams involved in digital security incidents. In the Netherlands, there are a number of official CERTs of large organisations involved in combating cyber incidents, such as the NCSC, the IBD, the Ministry of Defence, telecom organisations and banks.
Incident Response Plan
Know what to expect in the case of a IT security incident. Read more about the Incident Response plan.

